In SharePoint, the concept of policy enforcement is different than security.Security features of the product are used to stop people from accessing secured information and policy enforcement solutions are there to control and limit what users can do with the information once they gain access.
The following figure shows how security and policy enforcement solutions in SharePoint work hand in hand to help you protect and secure your information:
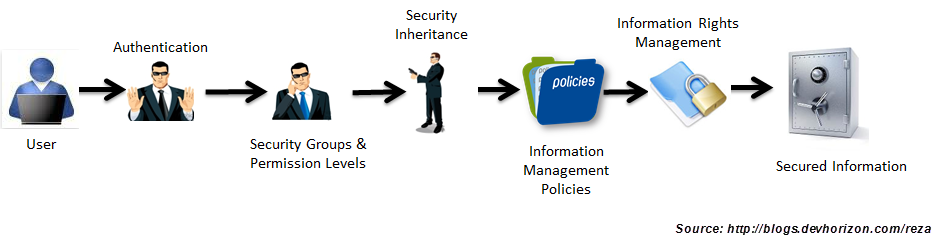
At a very high level, security features of SharePoint are handled at three stages:
1) Authentication : A process in which users prove they are who they claim to be. Typically, SharePoint externalizes its identity management business to other technologies like IIS, Active Directory, SQL Server, Windows Identity Foundation (WIF) and Forefront Identity Management (FIM), to name a few, and relies on standards and identity metasystems like SAML, Trust, Federation to enhance information security, and enable interoperability.
2) Authorization: Once a user is authenticated and gains access to a SharePoint site, what they can do in the site is important and is primarily determined by a separate process called authorization. SharePoint uses security groups and its extensible permission levels to perform authorization and to adjust a user’s access level to various objects such as sites, subsites and information in those containers. Note that you can use Claims to make authorization decisions in SharePoint too, but that’s out of the scope of this discussion.
3) Security Inheritance : SharePoint security model is designed based on the concept of inheritance . Just as an FYI, inheritance has nothing to do with writing your will or your grandchildren taking over your properties! Most of objects in SharePoint such as sites and documents can inherit the security permissions of their parents or they can have their own security scheme.
Audience Targeting is not a security feature in SharePoint. It has never meant to be like that either! It’s a CSS hack to hide/unhide and to tailor information to specific group of people (an audience group) and should never be used as a mechanism to secure content.
Once a user passes the security barriers mentioned above, there are two primary policy enforcement solutions in SharePoint to further control what needs to happen to the information they consume and interact with:
Information Management Policy: Information Management Policy is a set of rules that define certain behaviours or restrictions on information stored in SharePoint (only to information stored in SharePoint). For example, auditing accessing and modifying secured information is a popular need for many departments such as HR which can be easily implemented using Information Management Policies.
It’s important to note that information management policies in SharePoint can also be used in other use cases such as labeling and retention which has nothing to do with securing information.These policies are created and put in place to ensure your organization stay compliant. What makes Information Management Policy a powerful solution to enforce your organizational policies is that you can create your own custom policies or plug in 3rd party solutions to SharePoint. It’s an extensible framework!
Information Rights Management: People often confuse Information Management Policy with Information Rights Management. Well, they may look the same but they’re two different technologies with a little bit of overlap! I will cover the overlaps in future posts.
One problem with enforcing policies through Information Management Policy is that it only captures and intercepts user interactions with information kept in SharePoint. How the interaction is done is not important. It could be through Office Clients or Office Web App or even the browser, but the information has to stay in SharePoint in order for the policy to applly. Once the information is taken offline (i.e. download), there is no way to apply those policies to local copies.
Unlike Information Management Policies which is purely a SharePoint-y solution, Information Rights Management policies apply to both online and offline information and works across the board in SharePoint, Office client apps, SharePoint Workspace, Office Web App and Exchange, regardless of where the information is stored and how it is accessed.
Here are a few scenarios that an organization can benefit from using Information Rights Management :
|
Scenario
|
Usage
|
| Highjack-Proof Information |
HR managers can choose to protect downloads from certain HR sites, sections or sub-sections. When a user attempts to download a HR document, system will verify that the user has permissions to the given file, and issues a license to the user that enables their access to the document. System will then download the document to the user’s computer in an encrypted, rights-managed file format which is valid for that user only. If the information is stolen from that user’s computer or secretly copied to another computer, the hijacker won’t be able to open the document. |
| Online-Only Information |
HR managers can choose that some information can only be viewed online and only a subset of authorized users can print them and create hard copies. |
| Information Licensing |
HR managers can choose the number of days for which the license is valid. After the specified number of days has passed, the license expires, and the user must download the file again from the HR site |
| Premature Information Disclosure |
HR managers can choose to remove information protection after a certain date. For example, HR managers may want to make certain information public when off-boarding process for an employee is completed. Before such a date, however, they want to restrict access to such information to prevent premature disclosure. |
In the next blog post, we will talk about Information Rights Management in more details.